Healthcare Personnel Authorization Control: Best Practices & Software Development Tips

In this article, we will delve into the importance of healthcare personnel authorization control, exploring its key components and defining best practices for implementation. We’ll also touch on the role of staff training and education, discuss technological solutions, and provide real-world examples of successful healthcare staff authorization control implementation.
| ⚠️ Do you need immediate help with access control solutions for healthcare staff? Our engineers can assist you in building a system to meet those needs. CONTACT US FOR ASSISTANCE → |
In this day and age, when the exchange of sensitive healthcare information is increasingly digital, the protection of medical data has never been more critical. The term healthcare personnel authorization control may seem like a mouthful, but it encapsulates the very essence of securing patient data and ensuring that only authorized individuals and stakeholders have access to it.
Healthcare, like many other industries, has witnessed rapid digital transformation. Electronic health records development (EHRs), telemedicine applications, and interconnected healthcare systems have brought remarkable efficiency and convenience, but they’ve also created unprecedented vulnerabilities. The rise in data breaches and cyber threats has made it imperative for healthcare organizations to prioritize data security. This is where medical-personnel authorization control system development comes into play.

Learn more: ➡️ Custom EHR & EMR Software Development Services
Varieties of Access Control Systems Prevalent in Medical Facilities
Within healthcare facilities, there exists a spectrum of healthcare personnel access control mechanisms, including:
- Physical Access Control Systems: These systems employ tangible barriers like doors, gates, and turnstiles to regulate entry into specific areas within a healthcare facility. Keycards, PIN codes, and biometric readers are frequently used to either grant or deny access.
- Logical Access Control Systems: Designed to safeguard electronic information and data, logical access control systems employ measures like usernames, passwords, and other authentication methods to ensure that only authorized individuals gain access to electronic information.
- Visitor Management Systems: These systems are instrumental in tracking and overseeing visitors within healthcare facilities. Whether through traditional sign-in sheets, electronic visitor management systems, or the presence of security personnel, visitor management systems help maintain a secure, organized environment.
Each healthcare staff access control layer involves specific IT components and integrated solutions. We will primarily focus on the logical levels of access control associated with software solutions. However, similar approaches apply to other layers, as well, such as the IoT software solutions used in physical control systems for smart locks and other security devices.
? NOTE: To explore healthcare personnel access control best practices and implement them into your software, please feel free to contact one of our experienced health-tech consultants:

Slava Khristich
Healthtech CTO
Based in San Diego, Slava knows how to design an efficient software solution for healthcare, including IoT, Cloud, and embedded systems.
Table of Contents
The Key Components of Authorization Control
A crucial initial step in ensuring that only authorized individuals can access patient data within case management is to establish clear access levels and roles for different team members and stakeholders. These access levels and roles dictate who has the ability to view, edit, share, and delete patient data, and the specific circumstances under which such actions are permitted.
| ?⚕️? The Principle of Least Privilege (PoLP): This principle is at the core of authorization control. It dictates that individuals should only be granted the minimum access required to perform their tasks. In healthcare, this means that even within a single role, not all individuals should have the same level of access. |
For instance, a radiologist within a healthcare team may require full access to patient imaging records and diagnostic reports in order to accurately interpret and provide insights into a patient’s condition.
In contrast, administrative staff responsible for scheduling patient appointments and managing integrated medical billing systems may only need limited access to patient records, specifically designed for managing appointments and processing payments. If you want to create a custom healthcare medical billing and payment processing system, be sure to contact us for a consultation!
Adhering to the principle of least privilege in such cases ensures that each team member is provided with the level of access required to fulfill their respective role. This not only minimizes the risk of unauthorized data access, but also reduces the chance of data being misused or accidentally disclosed.
Key healthcare personnel authorization control components involve:
- User Roles, Access Levels, and Permissions: To implement effective authorization control, you must first establish user roles within your organization. These roles define the responsibilities of individuals and dictate which information they can access. Access levels and granular permissions further refine this control by specifying which actions each role can perform with the data based upon their professional function.
- Difference from Authentication: Authorization control is often confused with authentication, but each serves a distinct purpose. Authentication verifies user identity (e.g., with a username and password), while authorization control determines what that authenticated user can do. In essence, authentication is the key to the door, and authorization control is the mechanism that governs which rooms the key can open. ??
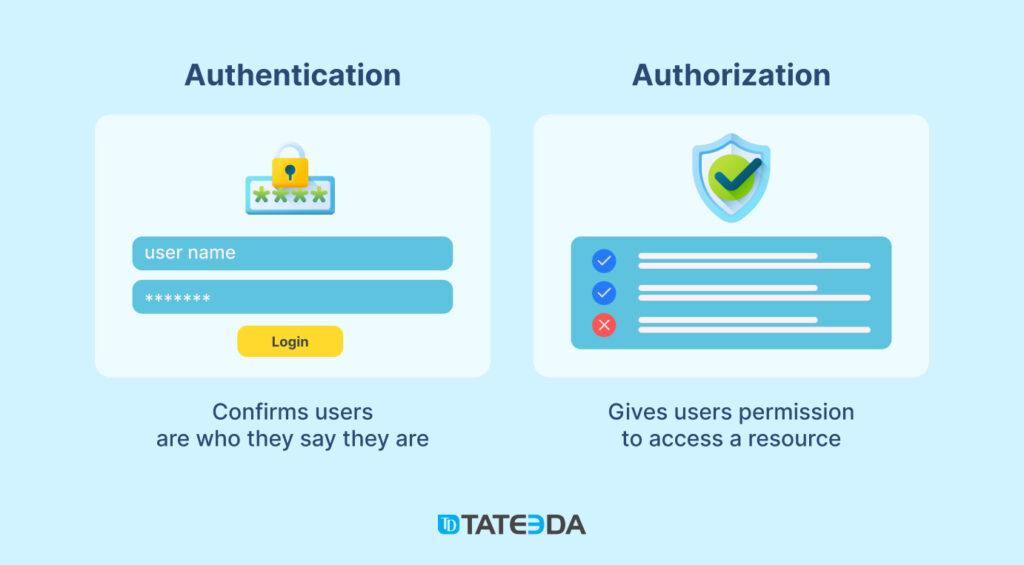
| ?⚕️? User authorization and authentication play a pivotal role in achieving medical staffing software compliance, as mandated by HIPAA. This foundational document outlines the fundamental principles of healthcare software security in the United States. By incorporating these essential regulations into medical staffing software, you guarantee the safety, reliability, and security of staff personal information. Learn more: ➡️ HIPAA Compliance for Medical Staffing Systems |
Medical practices can employ various models in the context of heightened security and streamlined access control for healthcare staff:
| Mandatory Access Control (MAC) | MAC is a stringent model in which access rights hinge on centrally determined security levels. Typical in government and military sectors, it employs security classifications (confidential and secret) for user clearance levels. MAC guarantees unalterable access criteria, securing sensitive data. ?️? |
| Discretionary Access Control (DAC) | DAC empowers resource owners to specify access to resources and permission levels. Resource owners configure the system, enabling authorized individuals to access specific resources. DAC offers flexibility but requires effective access-rights management. ?? |
| Role-based Access Control (RBAC) | RBAC restricts network access based on assigned user roles. Employees access information pertinent to their job roles, blocking unauthorized access. RBAC simplifies management by assigning permissions to roles, thereby reducing complexity. ??️ |
| Rule-based Access Control | Administrators create rules to govern access based on conditions such as time or user attributes. Access depends on specific user attributes, allowing granular control over permissions. ?? |
| Attribute-based Access Control (ABAC) | ABAC manages access rights by considering user, system, and environmental attributes. It enhances security by granting access based on varied conditions, providing flexibility and cost savings in access-control management. ?? |

| ??? User authentication, authorization, and role-based permissions are essential components of patient portal architecture. These gateways control patients’ access to their electronic records and appointments. We specialize in crafting customized, branded patient access portals for clinics and various healthcare facilities. Learn more: ➡️ Patient Portal Development Services |
Best Practices for Healthcare Personnel Authorization Control
Now that we’ve laid out the groundwork, let’s delve into the healthcare personnel access control best practices. At TATEEDA GLOBAL, we have our own preferred list of technologies we use for healthcare data management systems, including…
Role-Based Access Control (RBAC)
RBAC is a powerful strategy for healthcare staff authorization control. It assigns permissions to roles rather than individual users, making it easier to manage access rights. By adopting RBAC, you can ensure that each role within your healthcare organization has precisely the access they need and nothing more.
Consequently, every RBAC (Role-Based Access Control) system must operate within the framework of the following three fundamental principles:
- Role Assignment: In this context, a subject is permitted to exercise a certain permission exclusively if they have either actively chosen or been assigned a specific role.
- Role Authorization: The active role of a subject must be explicitly authorized within the system. This authorization process ensures that the subject’s role aligns with the intended medical data access privileges.
- Permission Authorization: Furthermore, a subject is only permitted to exercise a particular permission if that permission aligns with the role they are actively assuming. This linkage ensures that permissions are granted based on the subject’s role, maintaining a secure and organized access-control structure.
RBAC Best Practices for Healthcare Personnel Access Control (Example)
| In a hospital, the RBAC system assigns distinct roles to different personnel based on their job functions. For instance, doctors are designated the “physician” role while nurses assume the “nurse” role. Administrative staff are categorized as “clerks.” ??⚕️?? Each role is authorized with specific access permissions tailored to their responsibilities. Physicians can access and update patient records while nurses can view and update nursing notes. Clerks are limited to scheduling and billing tasks. This RBAC system ensures access aligns with staff members’ roles, preserving patient data security and streamlining their work responsibilities. |
Two-factor Authentication (2FA)
Combining 2FA with authorization control adds an extra layer of security to your healthcare software systems. Even if an unauthorized user somehow gains access to legitimate user credentials, 2FA will require an additional verification step, like a one-time code sent to a mobile device, before granting actual access. For even greater protection, additional levels of authentication can be incorporated as illustrated:
Regular Access Reviews
Access control should not be a “set and forget” process. Periodic access reviews are crucial to ensure that personnel have only the access they need. This helps in identifying and rectifying any unnecessary or inappropriate access promptly, thereby enhancing overall security and HIPAA software compliance.
Secure Password Management
Weak or compromised passwords can represent a significant threat to healthcare system authorization control. Enforce strong password policies, and consider using password-management tools to enhance security. Additionally, educating your personnel about the importance of strong, secure passwords is paramount to the fortification of your healthcare system’s defenses.
? NOTE: To explore potential options for establishing access control tools for your medical systems, please feel free to learn more about our services:
Custom Healthcare Solutions
See how we can engineer healthcare software, validate your ideas, and manage project costs for you.

Training and Education for Healthcare Personnel
Implementing best practices is only half the battle. It’s essential to educate your healthcare personnel about the importance of authorization control and how it reduces security risks for patient records and other medical data. Training should cover:
- The significance of safeguarding patient data.
- How authorization control works and its role in protecting data.
- The consequences of mishandling data or violating access privileges.
- How to recognize and report potential security threats.
A critical component of safeguarding healthcare data is implementing robust system/data backup procedures. Regular backups ensure that in the event of unforeseen data loss such as system failure, cyberattack, or natural disasters, critical information can be swiftly and efficiently restored. It’s essential for healthcare personnel to be aware of and trained in these backup procedures to ensure the integrity and availability of vital patient data.
By raising awareness and providing comprehensive training in both authorization control and data backup practices, you can empower your healthcare staff to become active defenders of patient data and continuity of healthcare services.
Technological Solutions for Authorization Control
There are various technological options and software solutions available to assist healthcare organizations in the implementation of robust authorization control. Each solution comes with its own advantages and considerations:
- Access Management Software: Specialized access-management software can streamline the process of assigning and managing access rights. It provides a centralized platform for role-based access control and permissions management. Examples include Okta, OneLogin, and Ping Identity.
- Identity and Access Management (IAM) Systems: IAM systems offer a comprehensive approach to authentication, authorization, and access control for healthcare staff, providing a holistic view of user identities and their associated access rights. Examples include Microsoft Azure Active Directory, Okta Identity, and Cloud PingOne.
- Blockchain Technology: Blockchain offers secure, tamper-proof record-keeping to enhance healthcare authorization control. It’s especially useful for maintaining audit trails and ensuring data integrity. Examples include MediLedger, HL7 FHIR Accelerator, and Hyperledger Fabric.
- Biometric Authentication: Biometric healthcare staff authentication methods such as fingerprint or facial recognition can further secure access to sensitive healthcare data. They are difficult to replicate and work to enhance security. A notable example is Apple’s Face ID.
? NOTE: If you want us to help you implement medical staff access control tools in your software, please feel free to learn more about our projects:
Delivered Healthcare Software Portfolio
The leading American healthcare companies benefit from working with us.
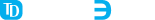
TATEEDA’s Case Studies: Healthcare Personnel Access Control Best Practices
One of TATEEDA GLOBAL’s clients, Travel Nurse Healthcare, required a system with three distinct protected environments for nurses, medical facility representatives, and company administrators.
We created different applications for each user group (role) with individualized interfaces and corresponding permissions. Thanks to enhanced medical staff access control, it requires two-factor registration and authorization. It also involves flexible permission management available to company admins.
In addition to this system, we created a time and material management system for IT and health-tech project teams that included extensive customization of user roles and a variety of access-control tools. This product, called BoB, allows you to create multiple user roles and contexts, including contractors, clients, employees, and more. Here, you can see an example of a system interface with permission configuration for a role:
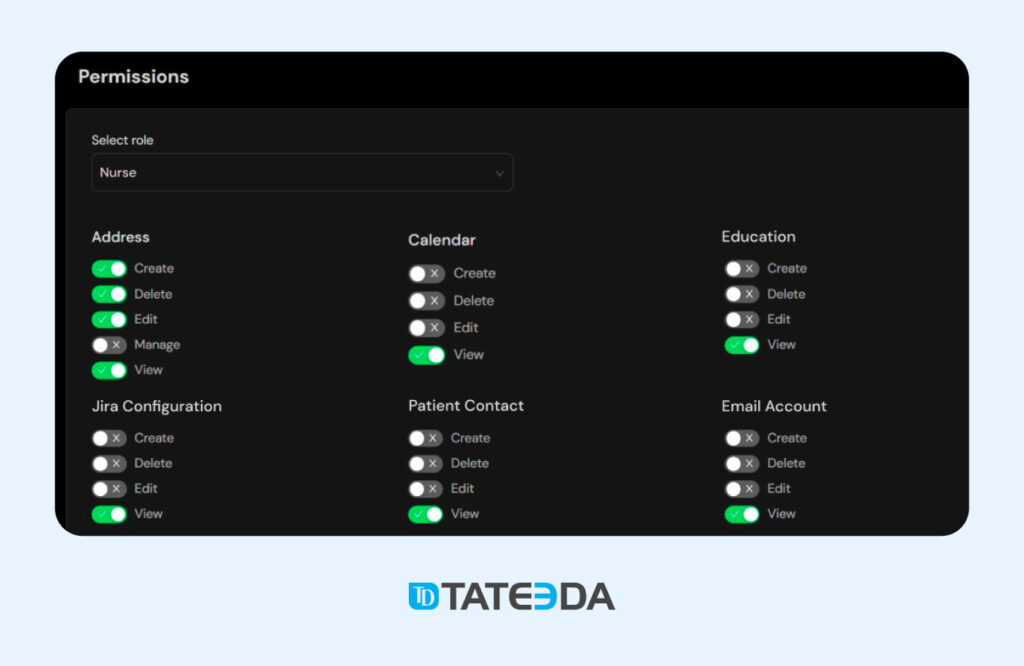
If you want a comprehensive medical-staff access solution for your healthcare facility or company featuring .NET programming, SQL, front-end development, back-end optimization, and security preparation, get help from TATEEDA GLOBAL. We guarantee a highly individualized approach and the best representation of your business logic in the context of healthcare personnel access control, including authorization, multi-factor authentication, and HIPAA compliance. Contact us today!
FAQ: Best Practices for Healthcare Personnel Access Control
What are the risks of inadequate authorization control in healthcare?
Inadequate authorization control in healthcare exposes sensitive patient data to unauthorized access, potentially leading to privacy breaches, identity theft, and medical fraud. It can also result in regulatory non-compliance, reputation damage, and legal consequences for healthcare organizations.
How does healthcare authorization control align with regulatory compliance, such as HIPAA?
Healthcare staff access control authorization plays a vital role in ensuring compliance with regulations like HIPAA (Health Insurance Portability and Accountability Act). By implementing robust authorization control measures, healthcare organizations can safeguard patient information, maintain privacy and security standards, and avoid legal penalties associated with non-compliance.
What role do training and education play in healthcare authorization control?
Training and education are integral to healthcare authorization control. They empower healthcare personnel to understand the importance of access control, recognize security threats, and follow best practices. Well-informed staff contribute to effective implementation of authorization control measures, reducing the risk of unauthorized access and data breaches.
How can healthcare organizations ensure patient data security through authorization control?
Healthcare organizations can enhance patient data security by implementing role-based access control (RBAC), conducting regular access reviews, enforcing strong password policies, and employing advanced authentication methods like two-factor authentication (2FA). Additionally, educating personnel about data security and privacy is crucial to maintaining a secure environment. TATEEDA GLOBAL can help you with the development and implementation of required software solutions.
What are the key components of healthcare authorization control?
The key components of healthcare authorization control include user roles, access levels, permissions, and the principle of least privilege (PoLP). These elements collectively define who can access, modify, or delete patient data, ensuring that individuals have the minimum access necessary to perform their specific job functions while reducing security risks.








![Best AI Development Companies [USA] Title Image](https://tateeda.com/wp-content/uploads/2025/11/Best-AI-Development-Companies-for-the-United-States-1-2.jpg)
