Digital Rights Management Software Development: Functions, Features & Services

In this article, we’ll speak about the main concepts of digital rights management (DRM) software. You’ll learn how it’s designed to protect and safely distribute protected digital property and files in accordance with appropriate licensing conditions.
We’ll discuss the basics of digital media assets protection, DRM-protected applications, technologies, and workflows involved in digital rights management development. In addition, we’ll review several DRM use cases and consider the key components of digital rights software.
| ⚠️ If you require help with the development and implementation of an intellectual property-protection product, please contact our engineers for IT assistance → |
The modern economy (especially the so-called innovation economy sector) features a highly developed concept of intellectual property (IP) that covers many types of intangible or digital assets created by the human mind, such as…
- Music, movies, and other multimedia content
- Architectural plans
- Tech specifications
- Inventions
- Literature
- Artwork
- Symbols
- Brand identity
- Software
- Designs
- Trade secrets
- Franchises
- And other types of intellectual products.
There exist many agencies, both nationally and internationally, that regulate intellectual property rights. This includes the World Intellectual Property Organization (WIPO) with 193 member states.
IP is legally protected and recognized by patents, trademarks, licenses, and copyright. The availability of these asset certifications grants their owners the exclusive right to use, distribute, and profit from them. Digital rights (a subtype of intellectual property rights, or IPR), on the other hand, refers to the permissions and restrictions that govern the use of digital media content like music, movies, visuals, and software.
| The modern world lives in a post-industrial paradigm, which means that IPR plays a vital part in the economy. For example, it is estimated that IPR-intensive sectors are responsible for almost 45 percent of the gross domestic product in the E.U., which is equal to 6.6 trillion euros and provides approximately 29% of all employment. It’s difficult to find any verified estimates of the world’s overall intellectual property worth; however, some sources offer tremendous business figures in the tens of trillions in U.S. dollars. |
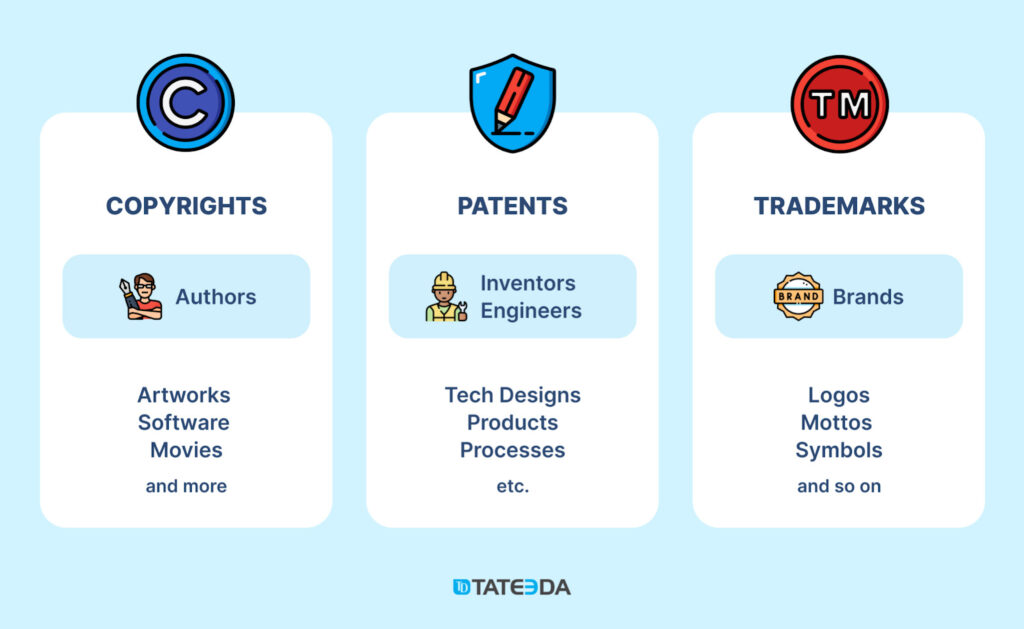
Table of Contents
Why Is Intellectual Property Management Software Important for Digital Asset Owners?
Your digital assets can hold substantial value, ranging from thousands to millions of dollars. Although your digital property rights are guaranteed by appropriate legislation in the United States and abroad, sharing, streaming, licensing, or distributing this proprietary content can pose the risk of losing control over your valuable intellectual asset materials because of irresponsible users and cyber-criminals.
The opposite of IPR is known as intellectual property infringement (or copyright infringement or content pirating), which describes the act of unauthorized (illegal) access, consumption, reproduction, display, alteration, or distribution of protected materials and products. Otherwise, it’s simply called virtual property theft.
Millions of IP infringements happen each year in the United States and worldwide. A recent trend indicates a growing number of cases involving artificial intelligence misconduct, such as training AI algorithms using inappropriately collected visual materials from commercial photo banks. When it comes to an issue with pirated multimedia content, such as illegally distributed movies or music, a massive growth of traffic to piracy websites was detected in 2022: a 15% increase, amounting to more than 185 billion visits to websites that brutally violate copyrights.
This is why all companies controlling digital assets must implement digital rights management (DRM) practices. It can be an acutely urgent case for software product development companies and all other businesses that own creative assets, including brands, documents, audio, video, logos, visuals, code sources, slide presentations, infographics, and websites. The DRM-protected approach involves a set of computer methodologies and technical tools that help companies safeguard their intellectual assets and materials against unauthorized access, misuse, and manipulation.
Basically, DRM practices and associated software systems are responsible for:
- Monetization of proprietary or protected content
- Protection, locking, and contracting of copyrighted materials & assets
- Compliance with local and international legal frameworks
- Distribution of digital asset licenses and updating of associated records like user agreements and license versioning
- Keeping track of the ways digital property is used by licensed accounts
- Detecting and resolving digital rights misuse or abuse cases
- Counterfeit and piracy prevention management.
Digital rights management software development is what helps companies create custom systems to keep their digital property safe and protected against theft and abuse. This can include an umbrella software solution combining multiple tools with different functions and purposes in the common DRM context. Before we delve into the details of DRM software development, let’s take a minute to learn more about our company and its offerings:
| TATEEDA GLOBAL is an onshore custom software development and IT staff augmentation company based in the United States (San Diego, California.) We offer our superior expertise and exclusive skills in building biotech applications, health-tech services, custom mobile app development, and web-based solutions for pharma businesses and medical staff management. We have qualified resources that are capable of providing a software solution set to keep your DRM-protected assets under full control. If you want to discuss potential services in the context of digital rights management technology, please book a free chat with our skilled IT engineer: |

Slava Khristich
Healthtech CTO
Based in San Diego, Slava knows how to design an efficient software solution for healthcare, including IoT, Cloud, and embedded systems.
DRM System Development: What Are the Main Functions of Digital Rights Management Software?
Digital Rights Management (DRM), or digital property restriction management, involves limiting user access to digital content. For instance, certain restrictions can be placed to prevent the use of media products by people who have no legit licenses or users whose licenses have expired. Specific scenarios depend upon each company’s business situation and protocols as executed by DRM software.
This type of software can be used to limit or manage the following actions applied to digital assets (files):
- Viewing
- Editing
- Copying
- Publishing
- Sharing
- Downloading.
At the same time, the DRM system is not a standalone software product, but a collection of software tools and technologies that can be mutually integrated and synchronized to control access to digital content and enforce usage rights according to the company’s policies and user requirements.

Digital Rights Management Technology: Which System Architecture Is Behind DRM Software?
DRM software architecture includes several electronic tools, controls, and system components required for the following functions:
- Software logic and admin/user interface for authentication and authorized access to digital assets, including viewing, copying, sharing, etc.
- Several layers of digital asset rights protection, including encryption, license management, multi-factor authentication, and secure login
- Encryption for valuable virtual assets, including safe file transmission channels for authorized users on demand
- Integration of blockchain systems and smart contracts (optional)
- Powerful database and content catalog management capabilities
- Reliable storage/repository for the digital content at rest.
In other words, DRM solutions can help you ensure the safety and security of your digital content and fair use by those licensed and authorized according to your business protocols. These practices usually require the following key DRM software components…
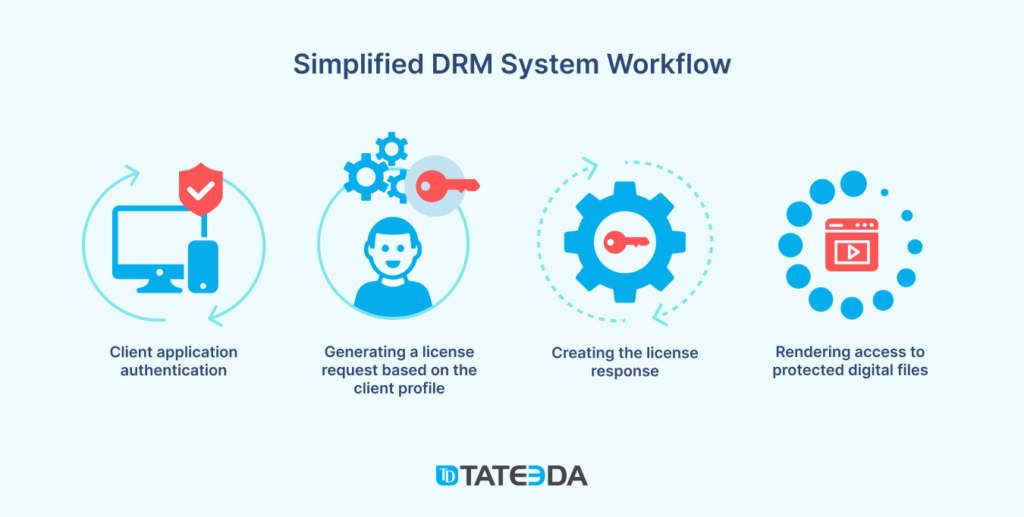
License Management Server Development
This server (or license engine) includes an intelligent DRM mechanism that automatically distributes licenses to users who have purchased or otherwise obtained premium/privileged access to the protected content. A licensing process can involve one or several options:
- Email or social media verification
- License codes, keys, or tokens
- Premium user accounts with special credentials
- Blockchain, token, and smart contract operations
- Device-based authorization and more.
Electronic licenses contain information about user rights and permissions, and are used to validate the user’s access approval for protected content. If you want to build a DRM server that ensures the best protection for your digital property, along with controlled distribution of user licenses according to a custom business workflow, please drop us a line. We’d be happy to discuss the potential architecture of your future custom digital rights-management system and provide an estimate for the project.
Digital Asset Encryption Implementation
If you don’t want your protected content or digital property to be easily accessible via technical means, it’s necessary to keep it converted into an unreadable form that can only be accessed by authorized users with proper authentication tools. Your choice of digital asset encryption model depends on your business and the DRM engineering decisions made by IT professionals in the context of each digital rights management project.
Your custom solution can include a combination of symmetrical and asymmetrical encryption techniques along with hashing and other appropriate encryption methods. Finding the perfect encryption formula for your project requires deep knowledge of modern cybersecurity standards. This is well within our area of expertise in health tech, biotech, and patient information-management industries. We are serious about sensitive data encryption and protection.

Authorization Mechanisms and Access Control
This technological layer involves several mechanisms responsible for verifying and identifying users in the context of their DRM profiles. The approach requires a comprehensive user interface and integration with a payment gateway, license server, and access control means. This conglomerate of software components can be automated with the help of AI, which coordinates and manages the following activities:
- Issuing new digital user licenses each time associated payments or other verification events are approved.
- Blocking or limiting access to digital assets for expired user licenses.
- Managing workloads and flexibly limiting the number of connected devices, locations, channel parameters, and users allowed to access protected content in a wide range of patterns and situations.
- Identifying, blocking, and/or flagging any suspicious user activity or attempts to inappropriately access protected content by using identity verification software.
Digital Content Outlet: DRM-protected Environment for Clients
One of the crucial components of digital rights management technology is how efficiently DRM-promoted limitations and restrictions are manifested at the client end of your digital asset-protection system. This can involve the following techniques and elements:
Client DRM Applications
Media players, marketplace apps, and more: Depending on the type of protected digital content you want to manage, it is possible to create a separate client application that works as a gateway for user authorization and access, unlocking content, distributing your digital assets, and marketing offers directly to users. One example could be an integrated video player application from a multimedia broadcasting provider like Netflix. This type of virtual content distribution medium works as an ecosystem, allowing clients to:
- Choose content they want to buy or unlock
- Select from the best marketing offers or plans
- Subscribe and pay for the service
- Unlock content using licensing codes, tokens, or email verification
- Consume and manage chosen content.
Digital Watermarking
In certain cases, DRM systems incorporate digital watermarking tools and other similar techniques (like audio watermarking) to embed traceable information within protected content. This information serves the purpose of identifying and tracing content back to the original source, asset owner, or licensee. Brand watermarks can be used to overlap movies, videos, documents, images, and other visual materials to assert legal ownership and highlight the unique identity of the content. This is one of the most effective ways to prevent or flag piracy attempts.

Additional DRM Security Tools to Prevent Illegal Content Use
- Restrict editing or reproduction of protected content
- Prevent saving of content to disallowed file formats
- Prevent downloading, sharing, and scraping of proprietary content
- Disable document printouts, text copying, screen-grabbing, and screenshots (if applicable.)
| If you are interested in intellectual property management software development… Work with TATEEDA GLOBAL. We have skilled resources for the engineering and implementation of DRM systems for a variety of content types: photobanks, streaming video services, document repositories, online music players, software websites, and more. We are highly experienced in the construction of web-based and mobile client-server services for medical, biotech, and pharma companies in the U.S., which are extremely concerned about patient privacy and data security. We have sophisticated experience in everything you may require for creating a top-notch DRM software solution, including encryption and user licensing. |
Custom Healthcare Solutions
See how we can engineer healthcare software, validate your ideas, and manage project costs for you.

How Does DRM Work? Specific Functions Executed by Digital Rights-management Applications
As we stated before, a DRM system can incorporate several crucial components or separate applications that can be smoothly integrated within a single holistic system or interconnected in another reasonable way. Overall, DRM is an umbrella term that employs various functionalities to ensure the security and controlled use of digital assets and content. Let’s delve into some key aspects of DRM features:
Watermarking for Ownership and Identity Verification
Documents and artwork can be digitally watermarked, embedding unique author or company identifiers that help establish ownership and verify or highlight brand identity. Watermarking acts as a deterrent against unauthorized use and provides a means to trace the source of leaked content (or at least recognize and promote genuine authorship.)
Expiry Dates and Time-specific Access Restrictions
With DRM, content owners can establish an expiry date or timeframe for their time-sensitive protected documents or digital content, thereby granting them precise control over the access and user license duration. When the predetermined expiry date arrives, users are automatically barred from accessing the content any further. Examples of this time-sensitive content include…
- Confidential reports and research findings in financial data, strategic plans, or proprietary information that are distributed to a limited circle of stakeholders or exclusive clients.
- Limited-time promotional content like special offers and discounts.
- Time-restricted educational materials from e-learning platforms, like course materials, lecture videos, or study guides.
- Preview copies: Trial versions and limited copies of books, music, software, or films distributed to potential users, journalists, critics, or influencers.
- Event-specific content related to presentations, session recordings, or event highlights from conferences, trade shows, meet-ups, or other live events.
- Digital products of limited availability, including software licenses, application evaluation copies, and other subscription-based services.

DRM Control & Restrictions: Prevent Digital Property Abuse & Pirating
Sometimes, users are not fully aware of digital asset rights (so they may abuse them unintentionally), or they ignore licensing conditions set by digital asset holders and deliberately carry out content pirating.
This is why, in addition to notifying users of digital property rights and limitations, it’s necessary to manage and limit all technical gateways for printing, sharing, editing, and saving protected digital assets and files.
DRM allows granular control over user actions, while content owners can specify the permitted actions, limiting them to align with licensing terms or copyright restrictions. These methods include the following:
- Sensitive content can be protected by DRM systems that disable the ability to take screenshots or screen snatches.
- Disabling of browser/system native options that could be used for unauthorized capture or redistribution of material (for example, blocking the right-click “Save As” option or the text selection and copying capabilities.)
- DRM applications allow content owners to restrict access to their digital assets based on IP address, geographical location, or specific device so that only a selected audience can access contact sources.
- Applying restrictions to web bots that might be used to parse and rip off content from websites in an automatic modality.
AI-enhanced DRM Software: Tracking Leaks and Eliminating Counterfeit Stores Online
DRM software plays a crucial role in tracking protected digital asset leaks by providing content owners with robust tools to combat unauthorized distribution and leakage of valuable intellectual property. With DRM solutions, content owners can embed unique identifiers, watermarks, and other types of digital fingerprints into their digital assets, making it possible to trace leak sources.
These identifiers help identify users or licensees responsible for instances of unauthorized use or illegal distribution. If a DRM software package features specific AI-driven components, it can:
- Automatically monitor various channels and platforms, including the Dark Web, where protected assets can be shared or accessed illegally.
- Detect and track digital asset leaks and alert content owners about their findings, including URLs, dates of appearance, and more.
- Once a copyright infringement case is approved, the DRM solution can either automatically generate and send an abuse report to website owners and their hosting provider, or help content owners file an abuse report.
- Empower content owners to take appropriate action against infringing parties, including separate cases of minor violations and deliberate piracy.
DRM software helps in the fight against large piracy hubs, counterfeit online stores, torrents, trackers, illegal online streaming websites, and so on. These websites attempt to sell unauthorized copies of digital content, deceiving consumers and infringing upon the rights of content owners. Appropriate legal action can then be taken, and the appropriate notifications can be filed with the help of DRM tools.
DRM Applications and Use Cases
Let’s consider several DRM use cases and examine digital rights-management cases and applications in action to get a better understanding of how DRM technologies work. This includes both general and high-level concepts for DRM applications specific to photo banks and video streaming services. These models are applicable to a variety of similar services, including e-books, vector visuals, music-streaming apps, games, and more, each with its own nuances.
Development of a DRM Solution for a Photobank Website: Protecting Digital Image Authorship
A photobank is a digital asset business repository of high-quality professional images used for various purposes such as marketing, advertising, publishing, blogging, and web design. Let’s explore some specific advantages that come with implementing a DRM toolbox in a photo bank:
- User Authentication: The photo bank’s website can incorporate robust authentication options like social media, email, and password authentication to safeguard premium account users and their associated rights or content assets. This ensures that only authorized users can access and utilize the copyrighted content.
- Watermarking: When new photos are uploaded to the photo bank and exposed to the web, an automated process can apply watermarks to these images. It is crucial to employ strong watermarking techniques that make it extremely challenging to remove the watermark, even when using professional photo editing tools. This helps deter unauthorized use and strengthens the identification and protection of copyrighted material.
- Subscription Plan Communication: A photo bank can use many different tools, including emails, tags, pop-ups, and more to effectively inform visitors about available subscription plans while providing clear details on the offerings, limitations, and responsibilities associated with each plan. By clearly communicating these terms, users are made aware of the rights and restrictions surrounding the use of the images, encouraging compliance and discouraging violations.
- Digital Asset Tracking: DRM systems can track and log the usage of images in a photo bank. This includes information such as who has accessed the images, when they were accessed, and how they were used. This type of tracking helps identify potential misuse and unauthorized distribution of images, and can assist in legal action, if necessary.
Preserving Video Authorship Rights: Developing a DRM Solution for an Online Video Platform
When it comes to safeguarding video content uploaded to websites or released on online platforms, ensuring content security is of utmost importance. Without proper protection measures in place, there is a risk of unauthorized downloading and misuse of video content. Thankfully, there are various methods available to protect digital content and prevent unauthorized copying or downloading of video files.
- The DRM process begins at the source: where the input video files are uploaded or transferred to a secure cloud storage solution (such as Amazon AWS). These files serve as the foundation for subsequent steps in the DRM workflow.
- Next, the input video files undergo encoding in which they are packaged and encoded into Adaptive Bitrate Streaming (ABR) formats such as HLS (HTTP Live Streaming) or MPEG-DASH (Dynamic Adaptive Streaming over HTTP from Apple). This encoding process optimizes the video for efficient streaming and delivery to a wide range of devices.
- Following the encoding stage, video files undergo encryption to add an additional layer of security. Digital keys provided by the DRM license provider are utilized during the encryption process to safeguard video content. Encryption ensures that video files are protected and can only be accessed by authorized users with valid licenses.
- Once encryption is complete, the video files are transferred to a Content Delivery Network (CDN) such as Amazon CloudFront. CDNs help ensure efficient, reliable content distribution by caching the video files across multiple servers in different geographical regions.
- When a user wishes to view a protected video, the video player initiates an authentication request from the DRM server. This authentication step verifies the validity of the license associated with the video file, ensuring that the user has the necessary rights to access the content.
- Upon successful authentication, the video player unlocks the video and grants playback permissions to the authorized user. The user can then enjoy seamless playback of the protected video content, knowing that it is safeguarded by DRM measures.
How Can TATEEDA GLOBAL Help You with Custom DRM Software Development?
By implementing the aforementioned DRM workflows, content providers can effectively fortify their digital files and assets, mitigating the perils associated with unauthorized copying, downloading, or misuse.
TATEEDA GLOBAL, a leading software development company, possesses the expertise to assist you in crafting DRM systems that establish a resilient framework to shield valuable video, photo, educational, visual, and audio materials.
With our solutions, you can ensure that your content is accessed and enjoyed solely by authorized users, aligning with the intended scope of licensing and distribution.
At TATEEDA GLOBAL, we offer the following comprehensive services:
- Development of web and mobile DRM applications or interfaces, enabling seamless access to your protected content repository while providing robust search functionality and granular control.
- Implementation of an automated watermarking mechanism for photos, videos, documents, and other copyrighted content, fortifying your assets and reinforcing ownership.
- Integration with existing DRM platforms and cutting-edge AI components to augment your content protection and tracking initiatives while harnessing advanced technologies to safeguard your digital material ecosystem.
- Skilled engineering and rigorous testing of DRM software tailored to the specific requirements and objectives of your diverse projects, ensuring optimum performance and reliability.
- Our extensive range of digital software development services encompasses a broad spectrum of solutions that can further enhance your business operations and digital ecosystem.
If you are seeking to establish a robust digital rights-management system for your enterprise, we invite you to reach out to us today for a complimentary consultation. In the meantime, please explore our portfolio of projects to gain insight into our expertise and capabilities:
Delivered Healthcare Software Portfolio
The leading American healthcare companies benefit from working with us.
FAQ: Digital Rights-management Software Development
What are the benefits of digital rights management?
- Protection of Intellectual Property: Safeguard the fruits of creativity and intellectual prowess by ensuring robust protection for copyright holders, authors, and valuable digital properties. With an impenetrable shield of DRM, your intellectual assets can flourish, bringing you well-deserved income and recognition.
- Secure Distribution of Digital Assets: Strike the perfect balance between accessibility and protection with a state-of-the-art DRM system. Defend your content against the relentless tide of piracy, making it arduous for infringers to violate your copyrights. With a meticulously executed DRM project, you can minimize the risk of compromised access to your invaluable intellectual property.
- Efficient Licensing Control: Seize the reins of control over your content like never before with DRM. Empower yourself as a content owner by dictating and enforcing licensing terms with precision. Specify usage restrictions, set expiration dates for licenses, and limit access to authorized devices, ensuring that your content is utilized according to your vision and business objectives.
- Revenue Generation: Unleash your potential for unprecedented revenue generation in the digital realm. DRM acts as a catalyst, providing you with the infrastructure, guidance, and tools to implement diverse business models. From subscriptions and rentals to pay-per-view, DRM empowers content creators to monetize their digital assets effectively, unlocking new financial possibilities.
Ready to harness the power of digital rights management for your business? Implement game-changing DRM technology and embark on a journey of enhanced protection, control, and revenue generation. Contact our team for more information!
How is digital rights management used in healthcare?
In healthcare, digital rights management (DRM) has emerged as a crucial solution to protect sensitive patient data while ensuring compliance with stringent data privacy regulations. Here’s an exploration of the specific applications of DRM systems within the healthcare landscape:
- Shielding Medical Records: DRM systems stand as a stalwart defense for electronic medical records (EMRs), shielding them from unauthorized access, copying, and distribution. Through robust data encryption and granular access controls, these systems enable healthcare providers to limit data access solely to authorized personnel.
- Preserving Clinical Trial Data: DRM systems extend a protective mantle to safeguard critical clinical trial data from unauthorized access, copying, or distribution. By employing advanced encryption techniques and enforcing usage restrictions, DRM systems effectively thwart competitors and unauthorized entities from gaining illicit access to valuable research data.
- Empowering Medical Device Security: DRM systems play a pivotal role in fortifying medical devices and maintaining control over firmware and software. By implementing stringent access controls, these systems prevent unauthorized modifications and hacking attempts on medical devices, ensuring that patient safety remains uncompromised.
- Ensuring Regulatory Compliance: DRM systems allow healthcare organizations to adhere to data privacy regulations like HIPAA and GDPR. By encrypting sensitive data and enforcing rigorous access controls, these systems help avert costly fines and legal ramifications resulting from data breaches while fostering compliance and peace of mind.
- Safeguarding Telemedicine and Remote Monitoring: DRM systems emerge as vital guardians of patient data in telemedicine and remote monitoring scenarios. Through robust encryption of data transmissions and meticulous access control enforcement, these systems bolster the privacy and security of patient information in these contexts.
What is the cost of building a DRM solution for your company?
This depends on the scope of work and the technologies involved in your project. An average cost can range from $50,000 to $100,000 or more. Contact us for a more precise estimate and other information!










![Best AI Development Companies [USA] Title Image](https://tateeda.com/wp-content/uploads/2025/11/Best-AI-Development-Companies-for-the-United-States-1-2.jpg)